Cyber Security is the buzz word everywhere in this fast-paced digital world. The more we digitize our lives, the more vulnerable we become. With the growing cyber-attacks, it is very important to safeguard your assets from these threats. The ICT Security industry is evolving day by day with the greater demands to secure the data & infrastructure. It is one of the fastest-growing fields that addresses the security risks of our increasingly connected digital world.
Organizations with public facing url are more vulnerable for such threats as they become the easy target for hackers to penetrate and take control. To secure such attempts, WAF — Web Access Firewall is one of the best tools developed so far.
Web Application Firewall (WAF)
Web Application Firewall (WAF) enables the protection of your web applications by standing between the internet traffic and your web applications. WAF monitors and filters out web traffic that travels to and from your application. protects web applications from a variety of application layer attacks such as cross-site scripting (XSS), DDOS, SQL injection, and cookie poisoning, among others. Attacks to apps are the leading cause of breaches as they are the gateway to your valuable data. Once hackers are able to break this barrier, it becomes easy for them to enter into your network and create chaos. This is your first line of defense which has to be robust to secure your infrastructure.
A WAF protects web applications by targeting Hypertext Transfer Protocol (HTTP) traffic. This is different from a standard firewall, which provides a barrier between external and internal network traffic. A WAF sits between external users and web applications to analyze all HTTP communication.
With my experience of managing WAF-As A Service for my global clients, I have noticed hundreds and hundreds of attempts every day from all over the world on the public facing URLs but with right configuration and block settings in place, these attempts were averted thus saving client’s valuable data every minute, every hour and every day. Below are some of those threat alerts SOC receives everyday –
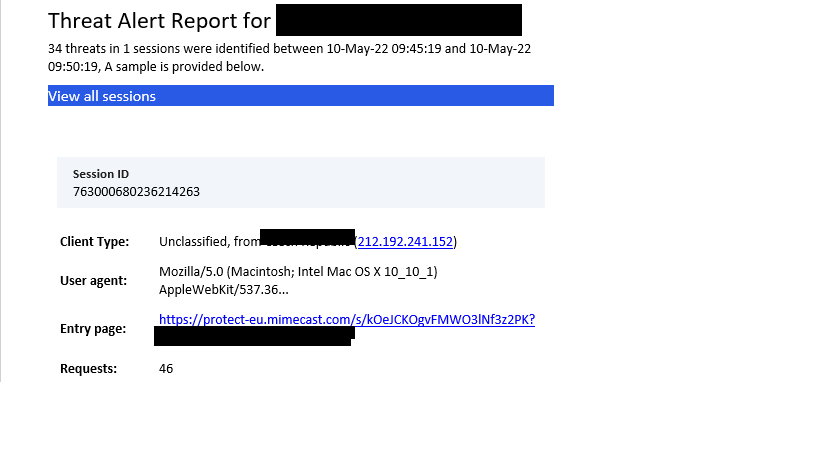
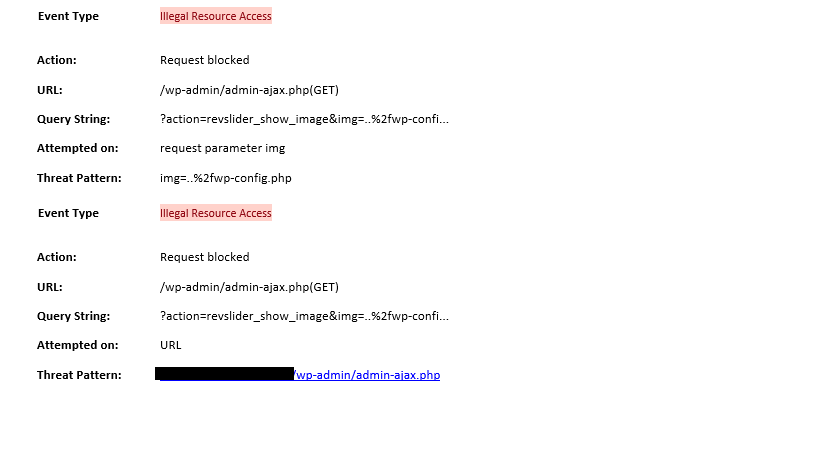
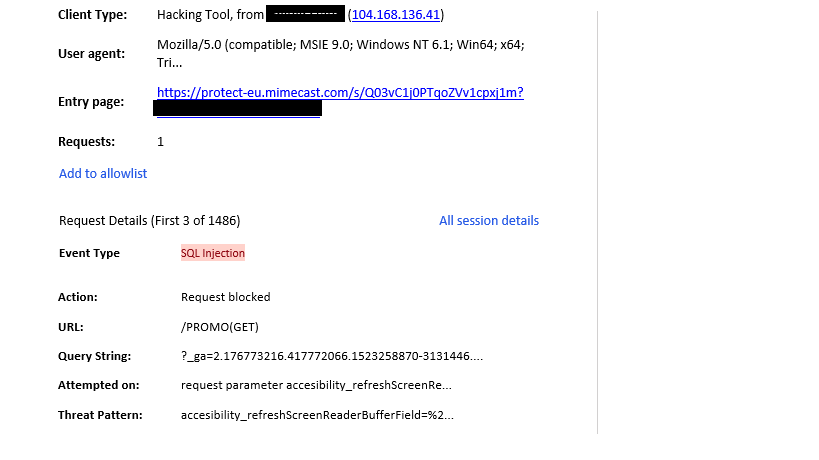
But with right block settings in place, these threats were averted.

Very informative blog… 🙂
Thanks for sharing this valuable info